Voice SDKs Network Connectivity Requirements
Info
The Twilio Client JavaScript SDK has been renamed to Twilio Voice JavaScript SDK.
The following article outlines Twilio's Voice SDKs' requirements for network connectivity. It lists the Twilio servers' ports and IP addresses that the SDKs must be able to reach, and the bandwidth required for quality audio.
Twilio's Voice SDKs assume a well-performing and accessible network; problems with firewall configurations, quality of service implementations, bandwidth allocations, and ISP performance are outside the scope of things Twilio can assist with and we will need to defer to your local IT, ISP, and hardware vendors for assistance.
- Choose the edge you will connect to and allow Media servers and Signalling servers .
- If you are using Global Low Latency edge, check the requirements .
- If you have access to Private Interconnect edges, you will need to allow these destinations .
- Ensure you meet the bandwidth requirements .
- Check the recommendations and best practices .
- Test your connectivity using this Network Test Tool .
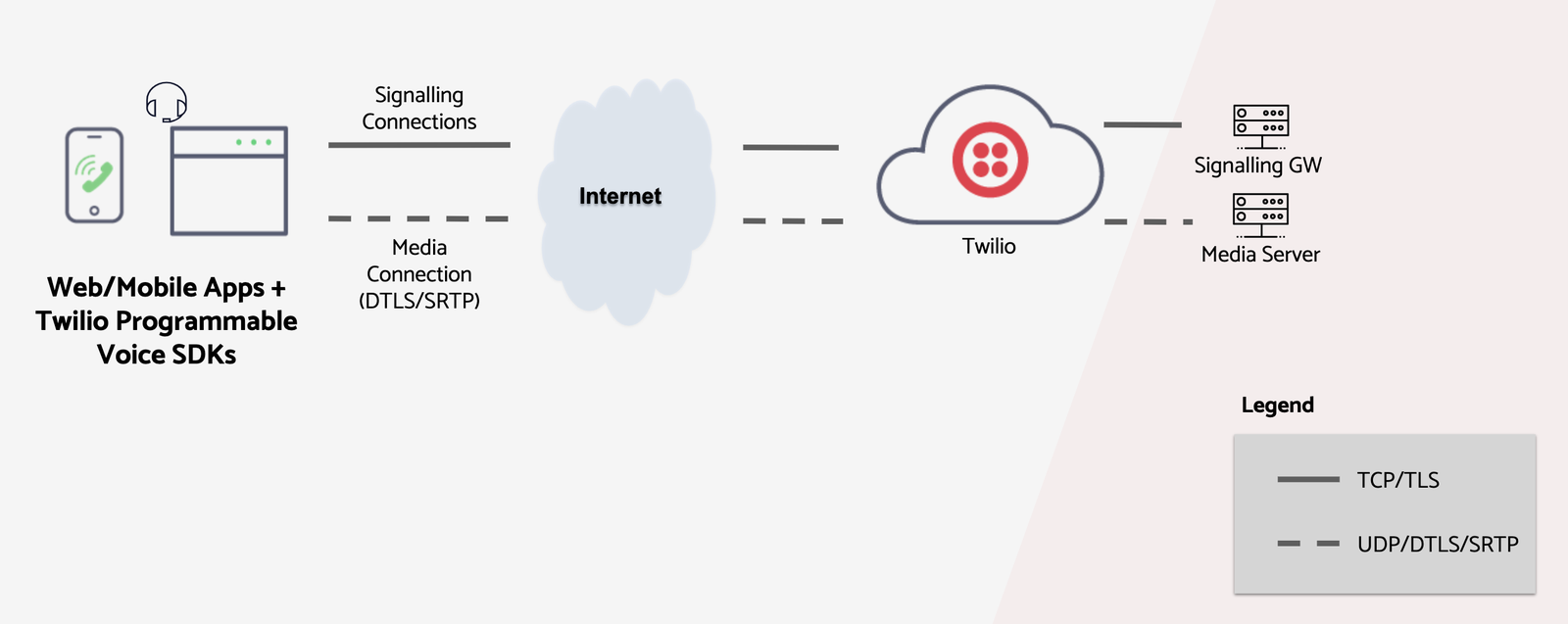
Applications using Twilio's Voice SDKs require connectivity to Twilio's infrastructure to be able to place and receive calls. As shown in the diagram below, two types of connections are required: Signalling and Media.
The signalling connection is a secure TLS connection that is used for sending and receiving control information to set up calls.
The media connection is a secure SRTP (Secure Real-time Transport Protocol) connection that is used to send and receive audio.
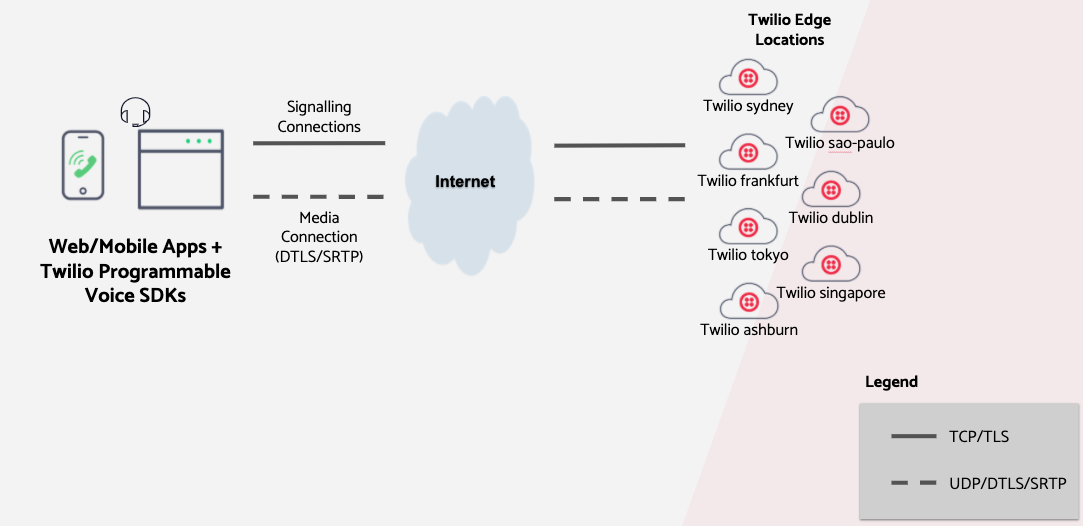
Twilio's Programmable Voice infrastructure is deployed in edges all over the world. By default, the SDKs use Global Low Latency (GLL) to determine the optimal Twilio edge to connect to.
In a typical organization network setup, a firewall is used to protect the private network hosts from the Internet. Firewalls are configured with rules to block or allow traffic to and from Internet destinations based on direction, protocol, and IP address.
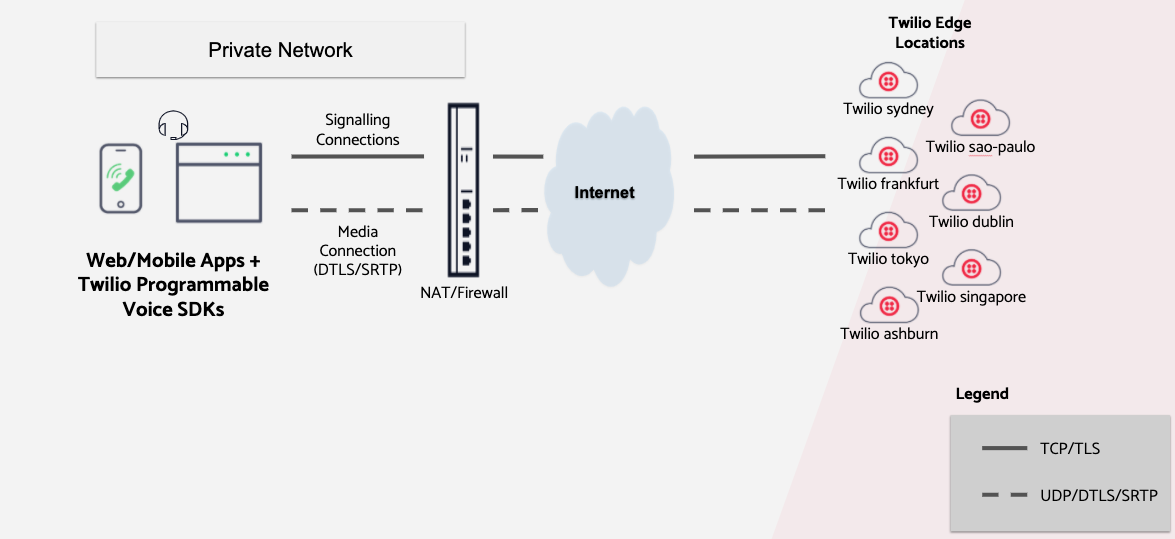
To access Twilio, your firewall should allow outgoing TCP and UDP traffic from your applications to Twilio's infrastructure and allow return traffic in response. Twilio will never initiate a connection to the SDK applications. Therefore, the firewall should not allow externally initiated connections back into the network.
In the Connectivity Requirements sections that follow, the required destination IP addresses and ports are listed. Your firewall should be configured to allow connectivity to the Media Servers and the Signalling Gateways corresponding to the SDK you are using.
Public Connections - Global Media IP Range
The Public Connections Destination IP Ranges and Port Ranges are now identical across all locations:
| Secure Media (ICE/STUN/SRTP) Edge Locations | Protocol | Source IP | Source Port † | Destination IP Ranges | Destination Port Range |
|---|---|---|---|---|---|
| sydney (au1 ) sao-paulo (br1 ) dublin (ie1 ) frankfurt (de1 ) tokyo (jp1 ) singapore (sg1 ) ashburn (us1 ) umatilla (us2 ) roaming (gll ) | UDP | ANY | ANY | 168.86.128.0/18 | 10,000 - 60,000 |
† The SDK will select any available port from the ephemeral range. On most machines, this means the port range 1,024 to 65,535.
Signalling requirements differ between the Voice JavaScript SDK and the Mobile SDKs. This section provides the connectivity requirements for each of these SDKs.
| Your Intranet | Allowed destinations | ||||
|---|---|---|---|---|---|
| Protocol | Source IP | Source Port † | Destination* | Destination Port | |
| Voice JavaScript SDK | |||||
| Secure TLS connection to Twilio signalling Gateway | TCP | ANY | ANY | chunderw-gll.twilio.com* chunderw-vpc-gll.twilio.com* voice-js.roaming.twilio.com | 443 |
| Secure TLS Connection to Twilio Regional Signalling gateways | TCP | ANY | ANY | chunderw-vpc-gll-{region}.twilio.com* {Where region is one of: au1, br1, de1, ie1, jp1, sg1, us1, us2} voice-js.{edge-location}.twilio.com {Where edge-location is one of: ashburn, umatilla, sao-paulo, frankfurt, dublin, sydney, singapore, tokyo} | 443 |
| Secure TLS Insights logging gateway | TCP | ANY | ANY | eventgw.twilio.com | 443 |
| Mobile Voice SDKs | |||||
| Secure TLS connection to Twilio GLL Signalling Gateway | TCP | ANY | ANY | chunderm.gll.twilio.com | 443 (10194 §) |
| Secure TLS Connection to Twilio Regional Signalling Gateways | TCP | ANY | ANY | chunderm.{region}.gll.twilio.com {Where region is one of: au1, br1, de1, ie1, jp1, sg1, us1, us2} | 443 (10194 §) |
| Secure TLS to Insights Gateway | TCP | ANY | ANY | eventgw.twilio.com | 443 |
| Secure TLS to Registration Server | TCP | ANY | ANY | ers.twilio.com | 443 |
† The client will select any available port from the ephemeral range. On most machines, this means the port range 1,024 to 65,535.
§ Mobile SDKs versions prior to 3.x require port 10194 instead of 443. If still using pre 3.x version, we recommend you upgrade to the latest version
* Destination names starting with "chunderw" is only used by Voice JavaScript SDK versions older than 2.3.0.
If you have access to private Interconnect connections, you will also be able to use one of the following values:
| Your Intranet | Allowed destinations | ||||
|---|---|---|---|---|---|
| Edge Location | Protocol | Source IP | Source Port † | Destination | Destination Port |
| ashburn-ix (us1-ix) | TCP | ANY | ANY | 208.78.112.0/25 | 443 |
| UDP | ANY | ANY | 168.86.128.0/18 | 10000-60000 | |
| san-jose-ix (us2-ix) | TCP | ANY | ANY | 67.213.136.0/25 | 443 |
| UDP | ANY | ANY | 168.86.128.0/18 | 10000-60000 | |
| london-ix (ie1-ix) | TCP | ANY | ANY | 185.187.132.0/25 185.187.133.0/24 | 443 |
| UDP | ANY | ANY | 168.86.128.0/18 | 10000-60000 | |
| frankfurt-ix (de1-ix) | TCP | ANY | ANY | 185.194.136.0/25 | 443 |
| UDP | ANY | ANY | 168.86.128.0/18 | 10000-60000 | |
| singapore-ix (sg1-ix)** | TCP | ANY | ANY | 103.75.151.0/25 | 443 |
| UDP | ANY | ANY | 168.86.128.0/18 | 10000-60000 | |
| tokyo-ix (jp1-ix)** | TCP | ANY | ANY | 103.144.142.0/25 | 443 |
| UDP | ANY | ANY | 168.86.128.0/18 | 10000-60000 | |
| sydney-ix (au1-ix)** | TCP | ANY | ANY | 103.146.214.0/25 | 443 |
| UDP | ANY | ANY | 168.86.128.0/18 | 10000-60000 |
† The client will select any available port from the ephemeral range. On most machines, this means the port range 1,024 to 65,535.
** Requires Voice JavaScript SDK 1.9.5+.
The following table lists the network requirements to deliver reasonable audio quality.
| Bandwidth (Uplink/Downlink) | Opus*: 40kbps / 40kbps PCMU: 100kbps / 100kbps |
|---|---|
| Latency (RTT) | < 200ms |
| Jitter | < 30ms |
| Packet Loss | < 3% |
* Opus codec is available from Voice JavaScript SDK version 1.7 and Mobile Voice SDKs 3.x
The Opus bandwidth requirements listed above are the default settings for Opus. Opus codec supports bandwidth control by allowing you to specify how much bandwidth it should use. See section recommendations and best practices below for how to configure Opus bandwidth requirements.
GLL is an AWS Route53 feature that resolves a hostname to the edge location with the least latency. This removes the need for the application developer to determine where the end user is connecting from or manually choosing which edge to connect to.
However, in order for GLL to give accurate results, the intermediate DNS must:
- Support RFC 7871 - Client Subnet in DNS Queries .
- Reside in the same edge as the SDK endpoint. For example, a host in the US configured with a VPN to Europe or configured with a DNS server that resides in Europe will result in connecting that host to Twilio edge in Europe
Warning
If the intermediate DNS does not support RFC 7871 and the upstream DNS IP address is an Anycast address, e.g., 8.8.8.8, then there is no guarantee Route53 will accurately determine the best edge to connect to.
To determine if your DNS supports GLL, use the dig or nslookup utilities as follows:
_10dig edns-client-sub.net TXT
_10nslookup -type=txt edns-client-sub.net
A DNS server that supports this RFC will have ecs set to True and contains an ecs_payload object:
_10;; ANSWER SECTION:_10_10edns-client-sub.net. 30 IN TXT "{'ecs_payload':{'family':'1','optcode':'0x08','cc':'US','ip':'34.225.44.0','mask':'24','scope':'0'},'ecs':'True','ts':'1588973397.05','recursive':{'cc':'US','srcip':'208.69.32.67','sport':'11807'}}"
A server that does not support this RFC will have ecs set to False:
_10;; ANSWER SECTION:_10_10edns-client-sub.net. 0 IN TXT "{'ecs':'False','ts':'1588973475.23','recursive':{'cc':'US','srcip':'76.96.15.65','sport':'54989'}}"
If you have a restrictive network and you specify GLL when connecting to Twilio, all media server IP addresses in all edge locations must be allowed. If you are not operating in all edges, we recommend you specify the edge that is closest to your deployment. With this approach, you will only need to allow the Media server addresses for the edge that you specify.
To select the edge, use the following snippet:
_13const device = new Twilio.Device(token, { edge: 'ashburn'});_13_13//or_13_13const device = new Twilio.Device(token);_13device.updateOptions({ edge: 'ashburn' });_13_13// Prior to v2.0, device.setup(token, { edge: 'ashburn' })_13// was used. As of v2.0, device.setup() is deprecated._13_13// Prior to v1.11 the region parameter was used._13// region is now deprecated, use edge_13Twilio.Device.setup(token, { region: 'us1'});
For best audio quality, your firewall should allow your local hosts to initiate the connection to twilio and send UDP (DTLS/SRTP) traffic to the Twilio Media servers.
However, If your network policy prohibits UDP connectivity, you can utilise Twilio's Global Network Traversal Service (NTS) to establish media connectivity over TCP or TLS. Please refer to the NTS documentation for a list of TURN servers and ports that will also need to be allowed.
Note, using TURN incurs extra charges as per NTS pricing. Refer to Global Network Traversal Service for more information.
The Opus codec has many advantages over PCMU and should be used by your applications. Opus is the default codec for Mobile SDKs.
To use Opus in your web application, use the following snippet when either instantiating the Twilio.Device or updating the Twilio.Device's options with .updateOptions(options):
_10const device = new Twilio.Device(token, { codecPreferences: ['opus', 'pcmu']});_10// or_10const device = new Twilio.Device(token);_10device.updateOptions({ codecPreferences: ['opus', 'pcmu']});
To set a custom bandwidth (16kbps), use the following snippet:
_10const device = new Twilio.Device(token, { codecPreferences: ['opus', 'pcmu'], maxAverageBitrate: 16000} );_10// or_10const device = new Twilio.Device(token);_10device.updateOptions({ codecPreferences: ['opus', 'pcmu'], maxAverageBitrate: 16000});
Twilio offers several solutions for private and secure connectivity to Twilio. See The Twilio Interconnect page for more details.